What is DHCP Port Security
DHCP is a key part of network management, and helps automate the process by allowing IP addresses to be assigned automatically along with configuration settings. But the very open nature of DHCP ports (UDP 67 and 68) also makes networks more vulnerable if these are not managed and secured properly. An unauthorized DHCP server may distribute false IP configurations, resulting in network troubles or security risks. In addition, denial-of-service (DoS) attacks can flood DHCP servers and bring a network down. To handle these risks we need to implement DHCP snooping, port security mechanism and awareness campaigns on cybersecurity. With the increasing threats of network skeletal cyber attacks, maintaining DHCP port hygiene through proactive management is more vital than ever to protect your users’ networks and keep their digital environments interconnected.
Importance of Cybersecurity Awareness Training
Some of the content from cybersecurity awareness training designed to enlighten staff about DHCP port security risks and best practices includes: Raising awareness is a way of enabling organizations to make their employees aware of the threats as they start recognising them and mitigate beforehand. This training creates an atmosphere of awareness and accountability among employees, for them to know the high importance of DHCP port security in protecting organization networks. With this information, employees are able to properly detect and address dubious activities associated with DHCP ports while adhering to security practices in order to mitigate risks. In addition, recurrent training teaches conscientiousness to the staff which ensures they keep updated with incoming threats and changing best practices as a whole helps strengthen the organization in terms of cyber-security resilience & preparedness.
What Causes DHCP Port Vulnerabilities
Rogue DHCP Servers:
Unauthorized DHCP servers can cause very serious problems by giving the wrong IP configs, potentially resulting in network outages or much worse a security vulnerability. When rogue DHCP servers hand out conflicting IP addresses or invalid network parameters, that can result in considerable networking disruptions as well as potentially even exposing the network to malicious activities. These breaches may lead to a loss of data confidentiality, integrity or availability and can result in man-in-the-middle attacks on unencrypted wireless transmissions. Features like DHCP snooping and network segmentation, powered by Preventive Security Measures such as handling the IP address allocation – should only have access to authorized DHCP servers that leverage root of trust enabled strong attestations-become essential for ensuring the integrity factor among all endpoints from a high point-to-point connection management perspective across your Network infrastructure(otherwise potentially threatened due to Quality-of-service outage or Rogue mismanagement)- it in turn reduces any potential disruptions introduced with introduction from associated security vulnerabilities.
Denial-Of-Service (DoS) Attacks:
Network-Based Attacks: Attackers may flood DHCP servers with requests to bring down the network and disrupt operations. These are the attacks collectively referred to by Distributed Denial-of-Service (DDoS), which attempts to overrun server resources, while at the end rendering it unreachable by legitimate client requests. Not only do these attacks disrupt network services, but they also put organizations at serious operational and financial risk. Secure Network Monitoring: To counter the threats mentioned above, effective and comprehensive network monitoring is needed along with intrusion detection systems (IDS) to monitor abnormal DHCP relay agents on traffic forwarding devices; 3 developments are necessaryTraffic Filter Technologies that can recognize and block malicious behavior by preventing unwanted locations from initiating Dynamic Host Configuration Protocol negotiations filtering based on IP address or device type. Cybersecurity awareness training helps the employees understand and mitigating tactics against DDoS attacks that impact DHCP infrastructure are vital in enabling network availability while maintaining robustness of an enterprise to adapt new security methodologies for incoming cyber threats.
The most common include Man-in-the-Middle (MitM) Attacks.
They can affect network traffic through manipulation of DHCP messages, and even steal or tamper with sensitive organizational data. Cybercriminals may use these unsecured DHCP protocols to redirect traffic MASQUERADE-like, perform MitM attacks or of data like IP addresses and network configurations. These breaches can violate network integrity and privacy respectively, so it is important that secure DHCP port security steps in where a man permanently weakens. Steps include using encryption protocols, watching for oddities in DHCP traffic and providing employees with thorough cybersecurity awareness training. These initiatives reinforce defense mechanisms against emerging cyber threats, making the network environment more resilient in today’s highly-interconnected digital world.
Cybersecurity Awareness Training Benefits
Risk Mitigation: Well-informed employees can rapidly detect boisterous DHCP actions like non-registered server presence or uncommon network behavior and notify IT security teams. This way, the proactive mechanism reduces any potential risk to turn into a major security incident and also helps keep network operation stable and sound. Raised employee awareness of DHCP port security further enables them to participate in protecting organizational resources from growing cyber threats, fostering a mindset mentality and accountability into cybersecurity practices.
Compliance: Training will either make it or break it that employees conform to the DHCP port security policies, procedures and all other requirements comically high enforced by regulatory standards. This helps in creating a compliant and responsible culture among organizations which further reduces the probabilities of various DHCP related security breaches. Having well-trained staff makes it easier for employees to use best practices and detect possible attack vectors – not only that, but they will also quickly respond in the event of an infection relating to DHCP, therefore improving network-wide security as a whole.
Response Readiness: Awareness training preps employees to respond appropriately in the event of a DHCP-related incident thus ensuring minimum disruption to your business. Teaching Employees about DHCP Port Security Risks and ResponsesHaving employees who are aware of the potential risks, and know how to respond to them improve your organizations resilience against network disruptions as well as access hacks. Ultimately, having your employees be proactive in these matters can significantly aid the prompt detection and mitigation of DHCP vulnerabilities to ensure organizational continuity and keep public trust in network integrity as cyber threats continue to evolve.
This is done by having a list of all the areas which DHCP Port Security Training Topics
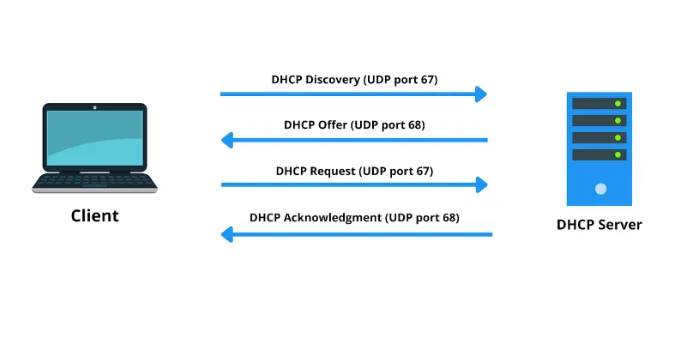
While we are getting into the specifics of DHCP, it is important to use that understanding what IP addresses does DHCP issue and how they do so; where UDP ports 67 & 68 fit into all this helps in knowing why a port would be used for security purposes to wreck havoc on operations. A. It dynamically assigns IP addresses: UDP port 67 sends client requests to the server and servers send configuration information;UDP since DHCP is based on clients, uses port number UDP68 which asks for an ip request from a specifiep_DHCP_SERVERIP.allocates manually.XtraBars both party This highlights the need to protect these ports against unauthorized access and solve can cause potential security problems in network environments.
Detecting Rogue DHCP Servers:
It is important to notice a rogue DHCP server if it appears, this could be an unauthorized way of handing out IP addresses or symptomatic for some other kind of network abuse. Any suspicious activities should be reported to IT security teams right away for further investigation and response. The removal of rogue DHCP servers avoids network outages and security breaches before they happen, keeping the organization’s networking infrastructure safe and sound.
Security Recommendations:
In order to protect yourself against DHCP-related threats, you should implement measures such as final securing the interface by DHCP snooping, providing protection at Layer 2 using port security or protecting it in Layer 3 with access control. Using DHCP snooping to validate the message is between a device and an expected upstream server, Port Security restricts access from unilaterally approved devices to shut-inside lanes on legitimate network-connected ports.ACLE Switch prevents unauthorized Spray Adapter data packets from being implemented in the adapter by allowing only whitelisted Bouncer data packet connections (blocking unknown MAC/IP addresses). These steps proactively reduce the risks associated with rogue DHCP server, unauthorized IP assignment or disruption of network services to make your overall DHCP port security more secure.
Incident Response:
Having the ability to respond promptly to report suspected DHCP incidents and apply appropriate containment methods when necessary is an essential component of network integrity. This ensures that IT teams are able to detect and respond as quickly as possible in the face of a threat, thus helping them minimize any issues on the operational or data protection side of things. Organizations can bolster their readiness and robustness to DHCP port security advancements by having clear procedures.
Steps To Building Effective Cybersecurity Awareness Programs
Periodic Training Sessions: Having regular training sessions are important to ensure employees remain up-to-date on the everchanging threats associated with DHCP port security as well as how best counter them. Staff were continually notified of DHCP ports and reminded to inherit the security architecture, best practice-style network device management habits, and prepared how-to quickly respond if attacked inside. Organizations then can enhance the security posture of their networks and reduce any potential effect that DHCP vulnerabilities may have on them by remaining vigilant, responsive in real-time via continued education etc.
Simulated Phishing Exercises: It is important to assess the response of employees through testing them with different DHCP related phishing tactics. These labs not only assess the technical DHCP port security, but also sharpen their alertness for identifying and responding to impending cyber threats. This helps organizations to continually send their workforce into battle-tested alertness and the proper stance against DHCP-printing cybersecurity risks, developing network resilience & security readiness as a whole.
Feedback and Assessment: It is important that you get feedback from your employees, to keep improving on how relevant it is to the DHCP port security training workscores). Organizations can do this by involving staff in the process and incorporating their feedback, ideas, and perspectives into training content-delivery methods, interactivity capabilities etc. By nature of being iterative, DHCP port security training continues to parallel the state-of-art threats and enterprise requirements maintaining a high level of awareness with employees covering an ever-changing landscape in cybersecurity risks.
Conclusion
Cybersecurity awareness training plays a vital role in strengthening DHCP port security within organizations. By educating employees about DHCP port vulnerabilities, best practices, and incident response procedures, organizations can enhance their overall network security posture. Empowered employees are better equipped to recognize and respond to DHCP-related threats, safeguarding organizational assets and maintaining operational continuity in an increasingly complex cybersecurity landscape.
Investing in DHCP port security awareness training is crucial for organizations looking to mitigate risks, comply with regulatory requirements, and foster a culture of proactive cybersecurity readiness.